Quick Links
Our Customers

More customers..
Rave reviews
![]() ...Crypto Obfuscator does a very good job of obfuscating code, doesn’t
add any further complications to my development cycle and is very affordable.
...Crypto Obfuscator does a very good job of obfuscating code, doesn’t
add any further complications to my development cycle and is very affordable.
- John Spano on GSPDevelopers
Full Review
Customer Speak
![]() I know you probably only get emails when people have problems, so I want
to make sure that I take the time to tell you how much I love this product
and how much it has enhanced my web-based application."
I know you probably only get emails when people have problems, so I want
to make sure that I take the time to tell you how much I love this product
and how much it has enhanced my web-based application."
- Alan Tepper, TepperWare Computer Solutions
![]() By using your components we were able to cut our time to add this feature
from weeks down to hours, it was just that easy (we may have not been
able to add this functionality at all within the timeframe we had given
ourselves)! We tried other components from other companies and we spent
more time trying to get them to add the basic features we needed when
your components had every feature we needed; easy synchronization of the
combobox and fileview, Vista folder thumbnail support (a definite plus
for showing previews of items in the folders), and more, which we continue
to find useful and implement in future versions of our products. If you're
a software developer, these
By using your components we were able to cut our time to add this feature
from weeks down to hours, it was just that easy (we may have not been
able to add this functionality at all within the timeframe we had given
ourselves)! We tried other components from other companies and we spent
more time trying to get them to add the basic features we needed when
your components had every feature we needed; easy synchronization of the
combobox and fileview, Vista folder thumbnail support (a definite plus
for showing previews of items in the folders), and more, which we continue
to find useful and implement in future versions of our products. If you're
a software developer, these
components are no-brainer"
- John Rennemeyer, MuvEnum, LLC
Other Products
CryptoLicensing
Add licensing, copy-protection and activation capabilities to your apps, libraries and websites using latest military strength cryptographic technology.
Visual Build Automation, Testing, Deployment And Release Management Software.
Crypto Logger
.Net Edition
Flexible high-performance logging library + powerful easy-to-use console
to view, search, manage and analyze log data.
EZNamespaceExtensions
.Net Edition
MFC/ATL/C++
Edition
Develop namespace extensions fast and painlessly!
EZShellExtensions
.Net Edition
MFC/ATL/C++ Edition
Develop IE toolbars, explorer bars, desk bands and all shell extensions
in fast and painlessly!
Windows Explorer-Like File And Folder Browsing Inside Of Visual Studio.
 Crypto
Obfuscator For .Net (v2020)
Crypto
Obfuscator For .Net (v2020)
Crypto Obfuscator For .Net is a powerful and easy-to-use product for code protection and obfuscation, performance improvement and optimization and improved and simplified deployment of your .Net applications. Here are its main features:
Symbol Renaming
Crypto Obfuscator renames all your class, field, method, properties, methods, parameter and generic parameter names to totally different strings. It is impossible to determine the original names from the new names. This makes it impossible for someone to try to determine the purpose or functionality of the renamed entity from its name.
| Before
|
After
|
Advanced Overload Renaming
Crypto Obfuscator can also rename fields or methods with different signatures to the same name. For example two fields having types int and boolean will be given the same name. Similarly two methods will different parameters will be given the same name. In the case of methods, the method return type is also used in the signature even though high-level languages such as C# and VB.Net do not support overloading by return type. The .Net runtime is able to differentiate between the fields/methods without any problem since the signatures are different. Needless to say, this scheme makes it even harder to reverse-engineer your code.
| Before
|
After
|
Fake Renaming Scheme
Crypto Obfuscator also has a renaming mode which renames all classes, fields, methods, etc to fake but realistic names like Domain/Log/Stream/etc (for classes) or Open/Close/Clear/Delete/etc for methods and so on. This makes it extremely difficult to differentiate between symbols excluded from obfuscation and obfuscated symbols.
|
Before
|
After
|
Automatic Exception Reporting
Crypto Obfuscator can catch any unhandled exceptions and automatically report them to a exception reporting service. The exception reports include full stack trace info along with the values of all method arguments and local variables, plus the system information, the time of exception and optional developer defined custom data. All exception reports can then be automatically downloaded from the service and examined from within Crypto Obfuscator. More Information
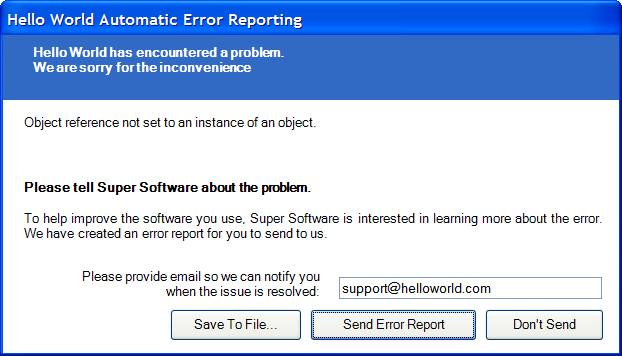
Method Call Hiding
Crypto Obfuscator can hide calls to methods and properties from external assemblies such as those from the .Net framework. In addition, it can also do the same for unrenamed methods and properties from the assemblies which are being obfuscated. This provides very strong obfuscation and makes it impossible to determine when, where and how such methods and properties are used.
| Before
|
After
|
Method Body (MSIL Code) Encryption / Code Virtualization
Virtualizes, encrypts, compresses and hides the MSIL code within methods. If the method is viewed by a decompiler or disassembler, only a single proxy call is seen.
|
Before
|
After
|
Advanced Tamper Detection
Crypto Obfuscator can perform strong name verification of the assembly itself even if strong-name verification has been turned OFF on the machine on which the assembly is running or if the assembly has been registered in the verification 'skip-list' - this is typically done by hackers or crackers. Furthermore, the strong name verification is done using the original key used to sign the assembly when it was processed by Crypto Obfuscator. Thus, strong name verification fails even if the key is removed or replaced - again something typically done by hackers or crackers.
Advanced Anti-Debug + Anti-Tracer Protection
Crypto Obfuscator's performs more than 10 advanced heuristic tests to detect if your software is running under a debugger or tracer. If detected, an exception is throw and your software will terminate. Both managed as well as native/unmanaged debuggers (including advanced debuggers such as OllyDbg) are detected. This provides a strong defense against crackers and hackers trying to debug or trace your software for various malicious purposes.
String Encryption
Literal strings often contain sensitive information such as login information, passwords, SQL queries, algorithm parameters. They also facilitate reverse-engineering of your .Net code. Crypto Obfuscator solves all these issues by encrypting all literal strings in your .Net code.
| Before
|
After
|
Constant Encryption
Constant values or arrays can contain sensitive information. They also facilitate reverse-engineering of your .Net code. When this setting is checked, constant values or arrays defined and initialized in code are encrypted.
|
Before
|
After
|
Control Flow Obfuscation
Many advanced decompilers can reconstruct the code in your methods including the exact structure of your loops, if-else statements, method calls, try-catch blocks, etc. This makes it very easy to revere-engineer your code. Crypto Obfuscator changes the structure of your code into spaghetti code while maintaining 100% the logic and output of the code. The result is that decompilers are unable to reconstruct the code structure and most of the times they crash while trying to do so.
| Before
|
After
|
Code Pattern Masking
Code Pattern Masking masks some commonly used code patterns like using, foreach, is/as, unboxing, creation of arrays/structures, typeof, overloaded operators, string concatenations and more. These code patterns are replaced by method calls which do the exact same thing, but whose purpose is not as easy to understand as the original code pattern.
|
Before
|
After
|
Remove Constant Field Values
When this setting is specified, Crypto Obfuscator will remove the value associated with all constant fields. Constant fields are defined using const in C# and VB.Net. The constant value specified in source code is not required after compilation and so it can be safely removed. This provides extra security as well as optimization.
|
Before
|
After
|
ILDASM Protection
ILDASM (Microsoft IL Dissassembler) is a free tool to disassembly any .Net assembly into MSIL (Microsoft Intermediate Language). Crypto Obfuscator can modify the assembly in such a way that ILDASM refuses to disassemble the assembly.

Resource Encryption & Compression
Many tools exist which can extract resources from your assembly. Such resources can often contain valuable, sensitive or copyrighted information such as images, UI (WPF BAML files), textual content, etc. Crypto Obfuscator can encrypt all such resources so that it is impossible to extract them from the assembly.
| Before
|
After
|
Assembly Embedding, Encryption & Compression
Crypto Obfuscator can encrypt all dependant assemblies and any additional assemblies you want into a single assembly. This makes it impossible for someone to get their hands on individual assemblies. You can use this feature to package all important and sensitive code/data into another assembly.
| Before
|
After
|
Watermarking
Crypto Obfuscator can embed watermark strings into your deployed assemblies. This can be used to track each assembly instance - this is commonly used for licensing by embedding user name and license codes as watermarks to deter license violations. The watermarks embedded in the assembly can be used in literal strings and constants to be used in your UI, message boxes, etc.
| Before
|
After
|
Metadata Reduction
Crypto Obfuscator can remove unnecessary or redundant information such as parameter names, property/event placeholders, etc from your .Net assembly . During symbol-renaming, Crypto Obfuscator will often assign extremely short (often single-character names) to your classes, fields, methods, etc. All these features can reduce the size of your .Net assembly considerably.
Duplicate String Elimination
Crypto Obfuscator can eliminate duplicate uses of the same string literal and replace them with one instance of the string. This reduces the size of your assemblies.
Runtime Performance Optimizations
Crypto Obfuscator can do certain changes to your assemblies which result in runtime performance improvements.
Additional Features
- Incremental Obfuscation
- Automatic Re-signing of assemblies using normal snk files as well as password protected pfx files.
- Automatic authenticode signing using certificates.
- Support for obfuscating .xap files.
- Exclude/Include classes, fields, methods, properties from obfuscation using Obfuscation Rules
- Exclude/Include classes, fields, methods, properties from obfuscation using inline Code Obfuscation Attributes
- Stack Trace De-Obfuscation
- Full support for debugging and pdb files.
- Visual Studio, MSBuild & ClickOnce integration.
- Automatic processing of satellite assemblies.
- Command Line Support - Integrate in your build process.
- And much more..!
Download Your Free Trial Now or Buy Now | Have a question? Email us
Quick
Links
Crypto Obfuscator For .Net: -- More
Info -- Download -- Buy
CryptoLicensing: -- .Net
Edition --- MFC
Edition --- ActiveX
Edition
Hyper Build: -- More
Info -- Download -- Buy
Crypto Logger For .Net: -- More
Info -- Download -- Buy
EZNamespaceExtensions: -- .Net
Edition -- MFC Edition
EZShellExtensions: -- .Net
Edition -- MFC Edition
VS Explorer for Visual Studio: -- Info
-- Download
Support: -- Technical
Support -- Articles
-- Case Studies
Company: -- About
-- Contact
Copyright © 2007-2020 LogicNP Software.


























